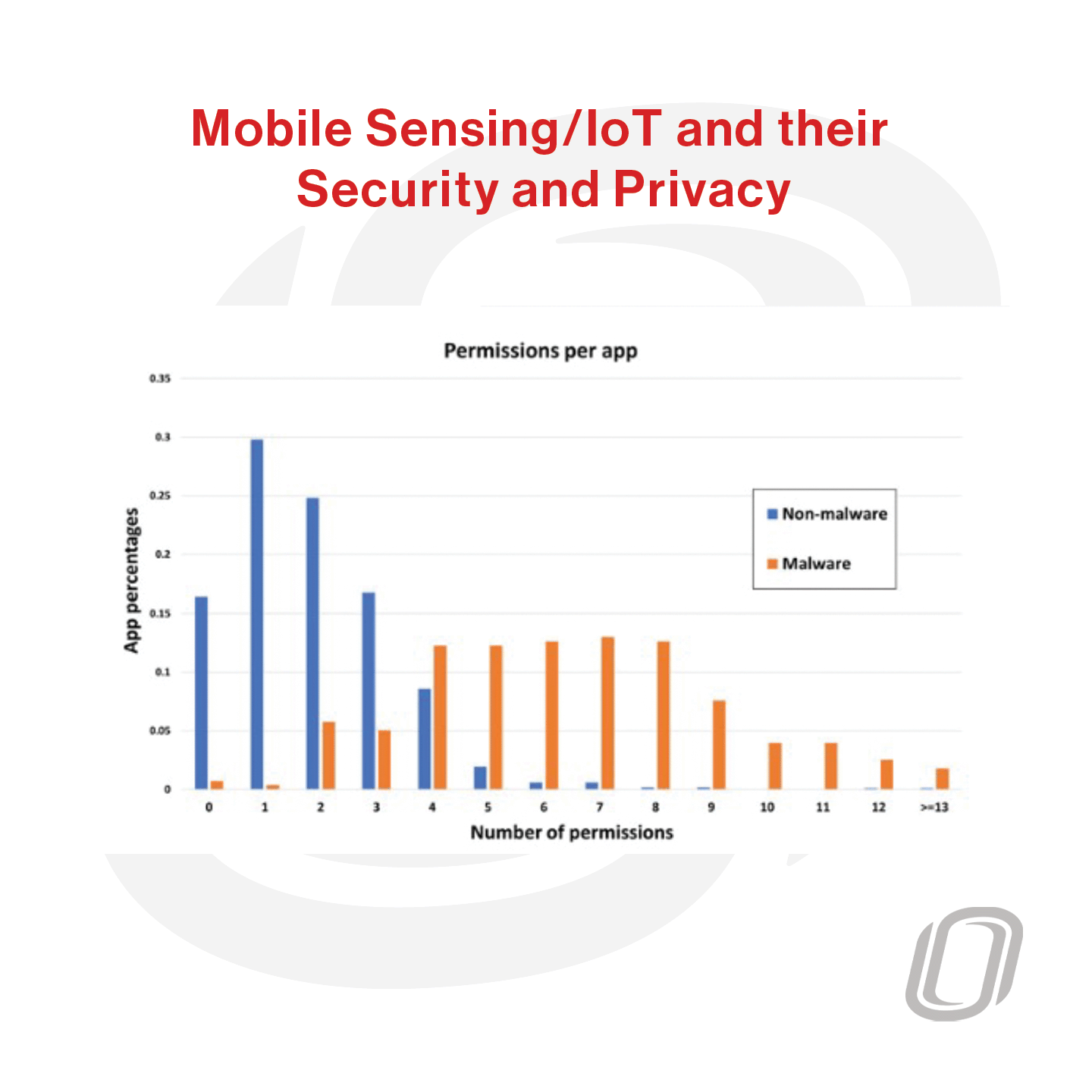
Projects
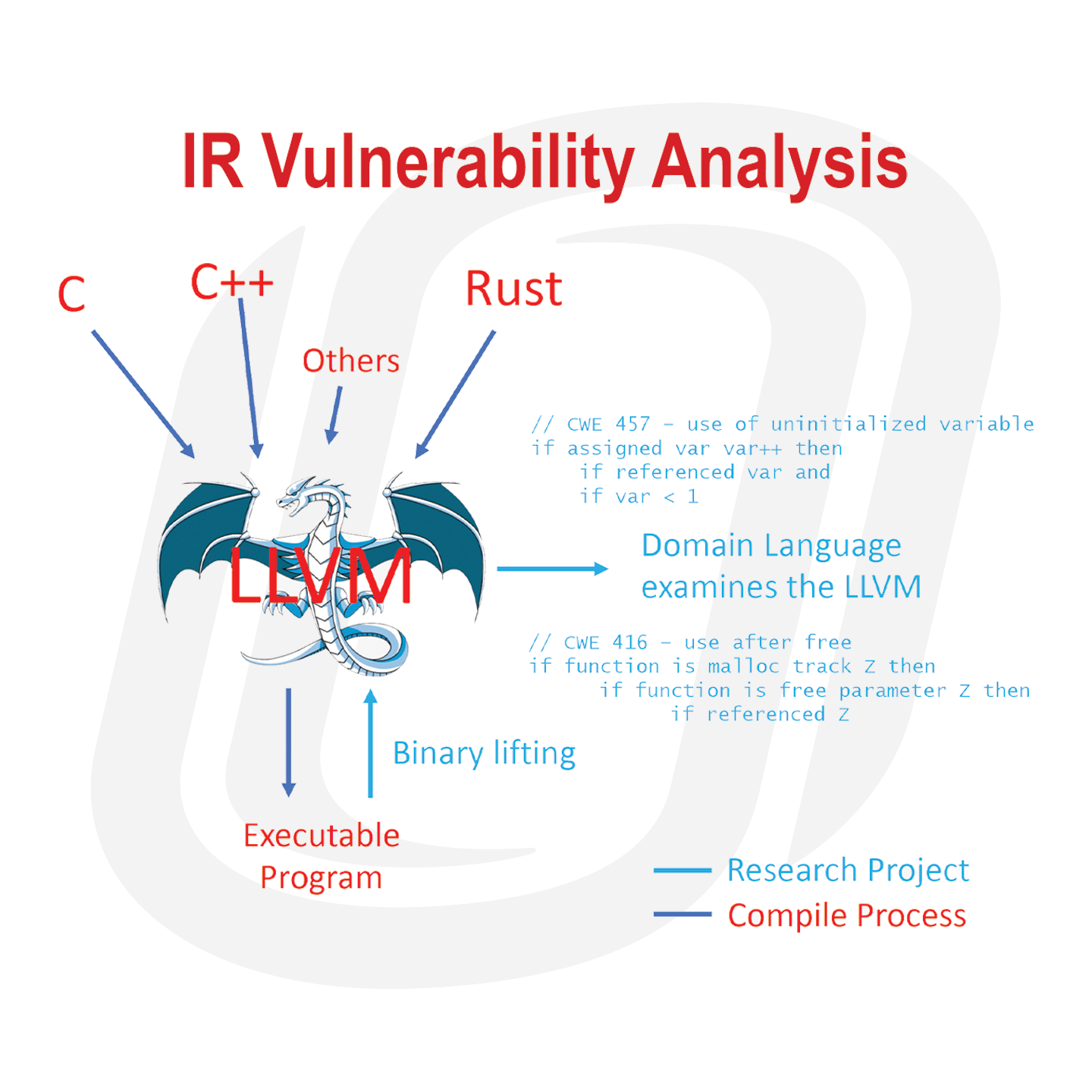
IR Vulnerability Analysis
Our team is designing a “domain specific language” to scan compiler intermediate representation (IR) code for specific potential vulnerabilities. By targeting the IR, the vulnerability scanning process is front-end- language agnostic; that is, the language the application is written in does not matter. And by “binary lifting”, converting...
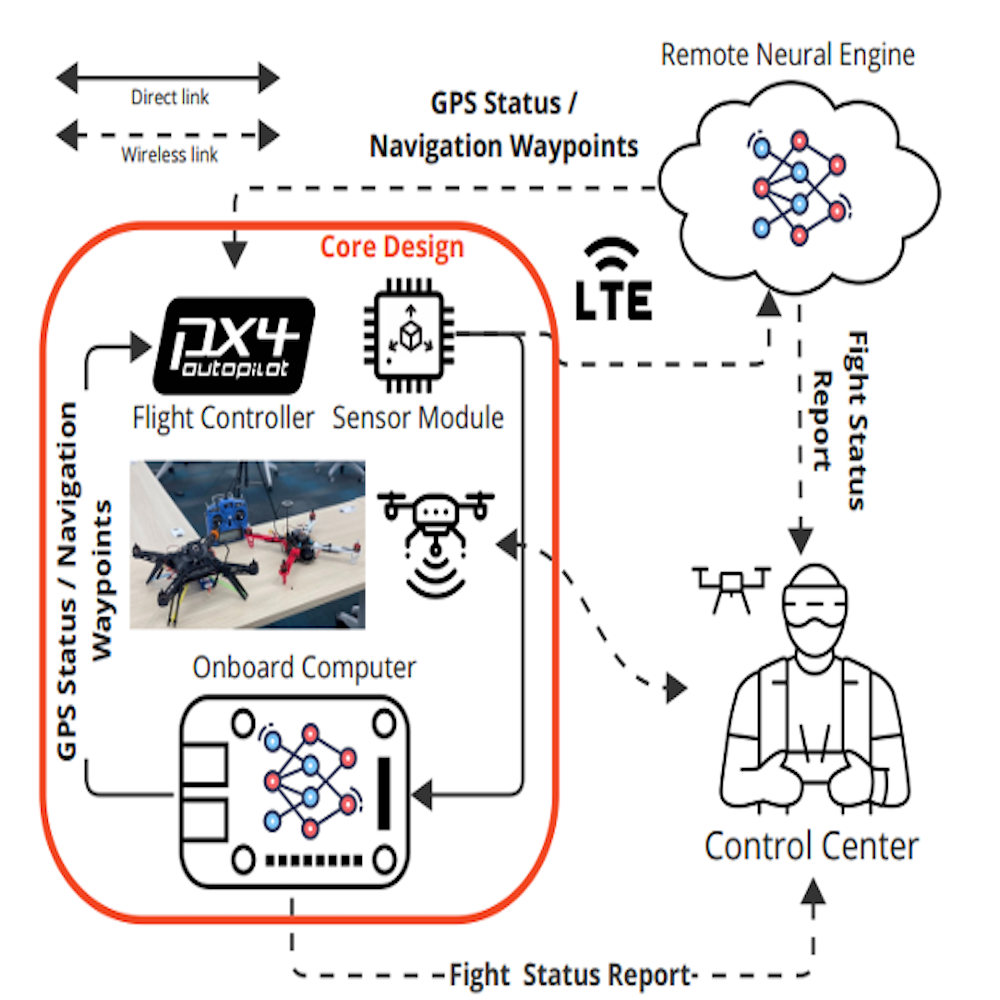
Cyber Resilient UAV Operation
This project aims to 1) investigate the existing GPS spoofing attacks targeting UAV systems and facilitate real-time detection of such attacks, 2) explore and develop a cyber-resilient GPS-free path planning and navigation scheme for UAVs using multi-modal sensor inputs, 3) leverage the Multi-Modal AI-enabled UAV Research (MM-AIR)...
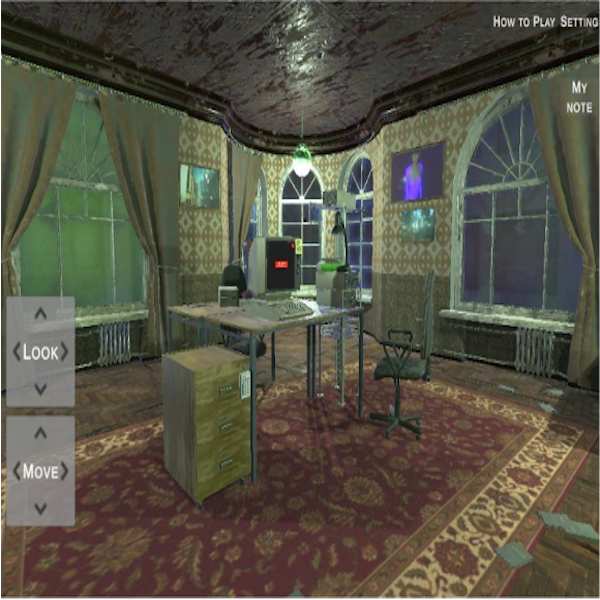
Immersive, Personalized, and Accessible Cybersecurity Training
The project will gamify cybersecurity training in a 3D immersive environment in which learners can navigate through connected rooms and labs while completing learning tasks. A fine-tuned large language model (LLM) will be integrated into the interactive environment as a personalized coach...

Enhancing Cybersecurity Awareness of American Indian Farmers and Food Producers: Nebraska Ponca Tribe
As information technology is increasingly integrated into modern farms, the food and agriculture industry has become a focal point for cybercriminals and nation-state actors. This project aims to create...

Identifying and Mitigating Cybersecurity Vulnerabilities in Farm Settings
The integration of IT into agricultural machinery and vehicles introduces a variety of cybersecurity concerns for the farming community: malicious actors gaining control of on-field sensors, changes to farming data...

Digital Forensic Investigations of Medical Devices
Increased frequency and severity of cybersecurity incidents impacting healthcare organizations has prompted the publication of best practices for these organizations, when attempting to respond to incidents in their respective settings. While these best...

Nebraska Deterrence Lab
Nebraska Deterrence Lab (NDL) is a multi-discipline that explores the complex multi-actor relationships that threats have on private, public and government sectors. Our focus areas of deterrence, quantitative risk, and analysis of data align with the needs of a wide variety of stakeholders. We educate the future workforce to innovate and think critically. We explore mechanisms to provide trustworthy, timely, and accurate information to facilitate decision making. We...

Congruent Threat Hunting
Threat hunting is used by private, public, and government entities to proactively search for threats that typically evade normal detection mechanisms. Threat hunting has evolved quickly in the cybersecurity industry, but the research surrounding the most effective methods for hunting are still maturing. Understanding and building new processes for threat hunters can not only improve how threat hunting is conducted, but also create new knowledge...

SMART Analytics for Critical Infrastructure inside a Resilient Data Fabric (SMART-RDF)
This project focuses on integrating multi-source field and historical data to monitor and predict the health of critical structures like bridges. We are creating a scalable technological framework, enabling real-time assessment of structural health and informing decision-makers. We collect continuous monitoring data from diverse sensors using a resilient data...
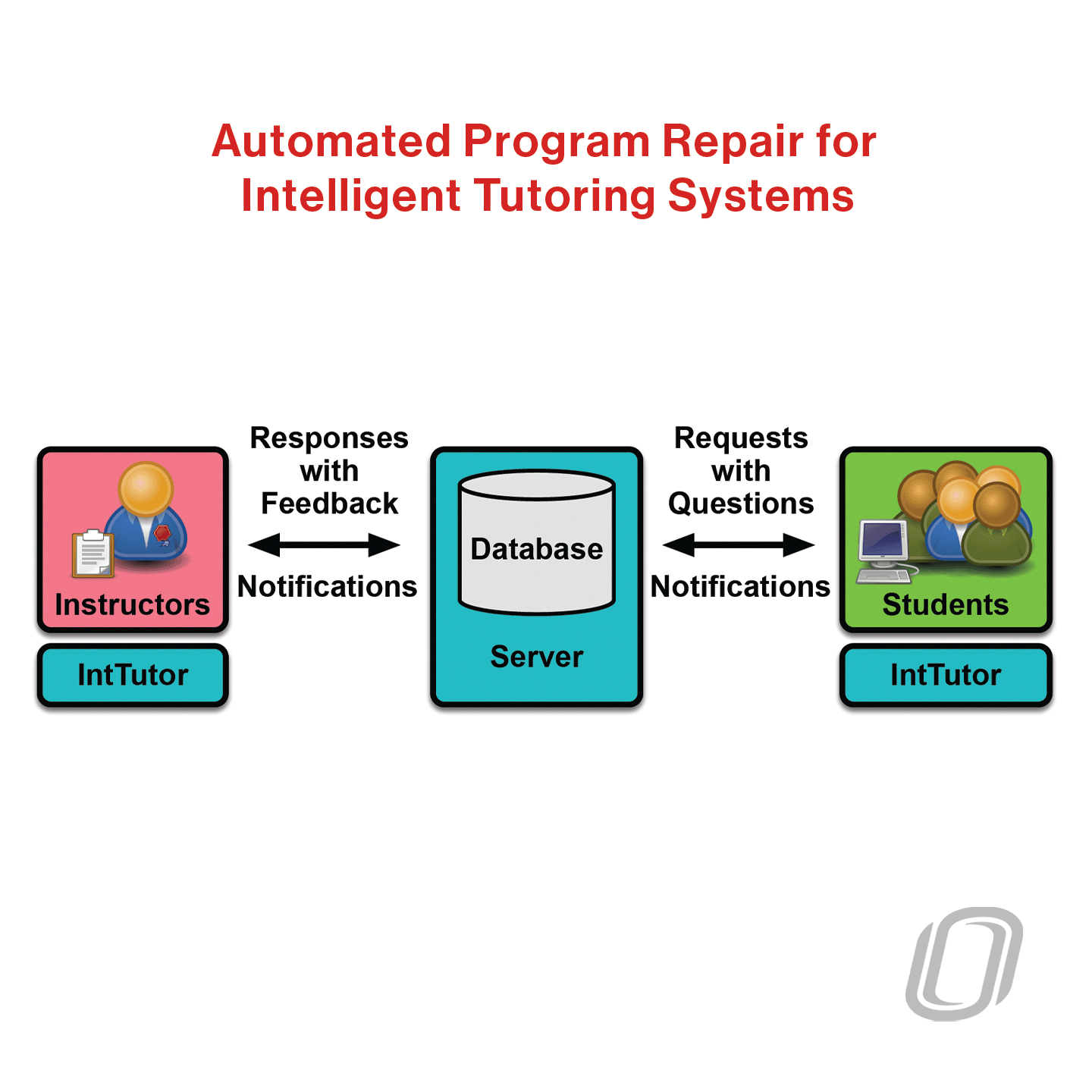
Automated Program Repair for Intelligent Tutoring Systems
Insecure program practices seriously threaten software security. Misusing security primitives in application-level code is not unusual. One big challenge is the lack of automated guidance on how to use existing libraries for secure coding. In this research, we present an Intelligent Tutoring System that automatically flags common cryptographic misuses and suggests possible repairs.

Behavioral Information Security
The majority of cyberattacks can be attributed to the human element (with over 74% of data breaches involving the human element, according to the Verizon Data Breach Investigations Report – DBIR 2023). This research investigates the human factors and motivations that influence behaviors such as clicking on...

Nebraska GenCYBR Camps
NGC hosts around 75 students per year from diverse backgrounds and experiences in the 6th to 8th grade band to increase their interest in STEM and cybersecurity. NGC is structured around immersing students in hands-on curricular activities associated with bite-sized integrable cybersecurity modules. Content from NGC has at minimum reached 90 teachers and over...
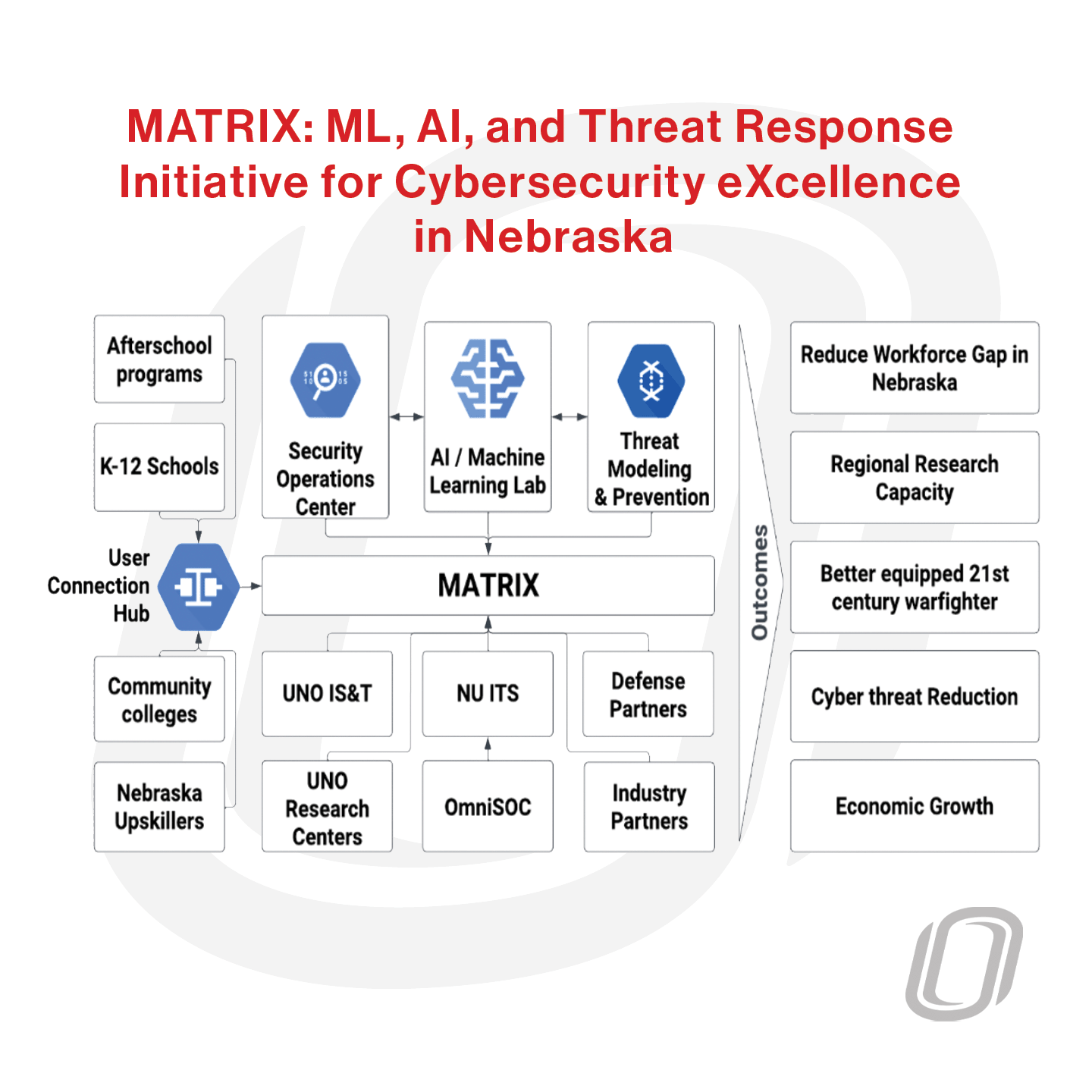
MATRIX: ML, AI, and Threat Response Initiative for cybersecurity eXcellence in Nebraska
Enhance Nebraska’s positioning in AI, ML, and Cybersecurity by developing an AI-enabled Security Operations Center (SOC) to monitor and respond to cyber threats in real time. Create a Lab to research new cybersecurity detective, preventative, and corrective...